Quick IPv6 Recap
IPv6 is the most recent version of the Internet Protocol and has been installed by default on operating systems for quite a while. In fact, Microsoft Windows released Vista with IPv6 supported and now every new Microsoft Windows operating system has it installed as well. Since IPv6 is enabled by default and preferred over IPv4, systems will prioritize available IPv6 network connections. Let's go over a few risks that this could pose in an enterprise environment. IPv6 being enabled (by default) and not being used presents an opportunity for a malicious threat actor to deploy a rogue IPv6 router onto the network. When either router advertisements are sent by the router, or the router answers IPv6 neighbor solicitations or DHCPv6 requests, a workstation with IPv6 enabled will (essentially) say "hey, I found an IPv6 router. I want to use that configuration instead of my current IPv4 configuration!"Understanding How This Works
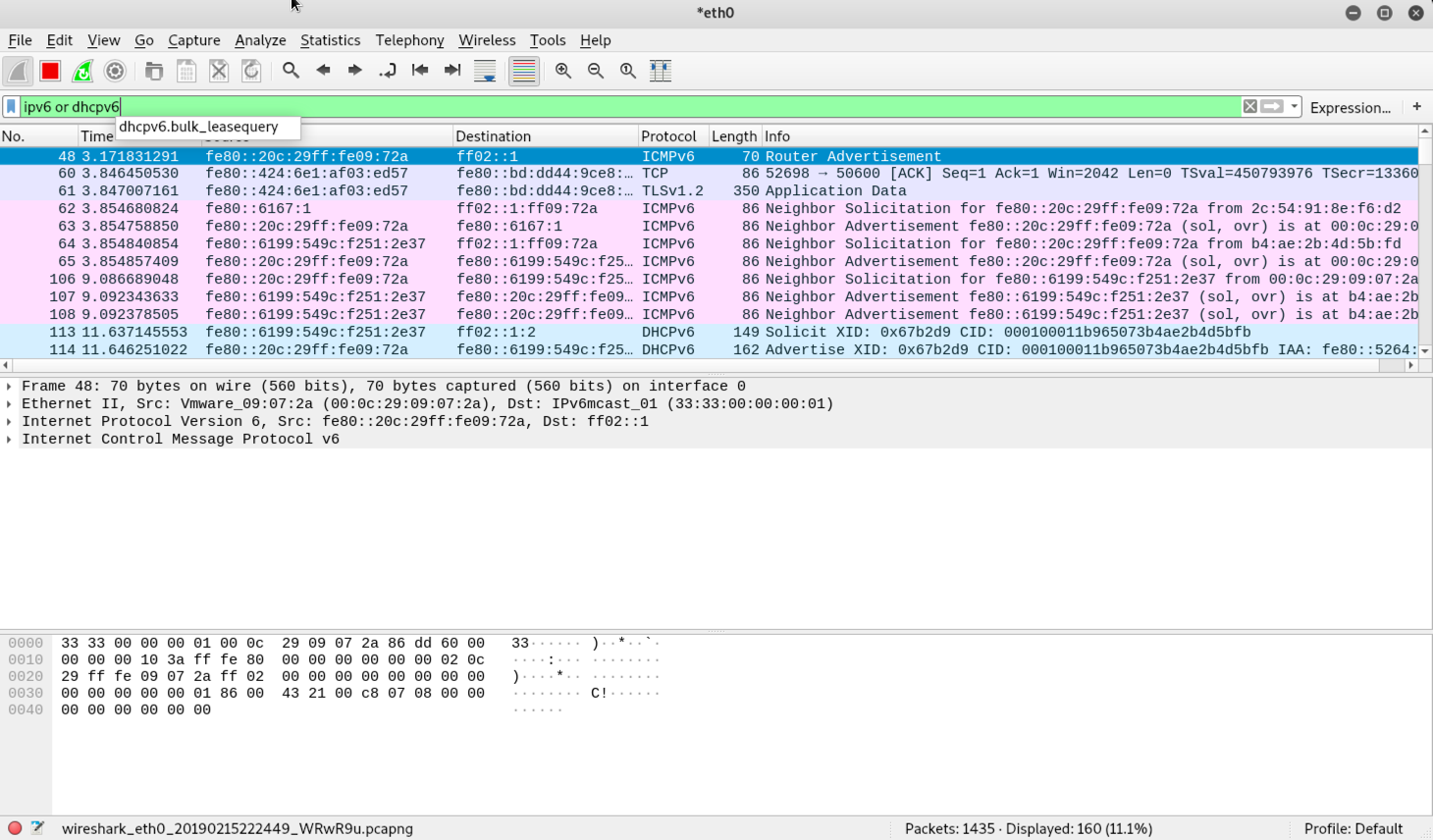
To get a better understanding of how this attack works, let's take a look at some broadcast traffic on the local network: Using tcpdump (sample snipped output)Using Wireshark
IPv6 and DHCPv6 traffic in Wireshark As you can see in both examples, there are several solicitation packets from an IPv6 client on the local network as it searches for an IPv6 router. An attacker could respond to these requests and provide DHCPv6 leases to clients. For a quick step-by-step packet analysis, let's take a look at what exactly is happening here: 1.An IPv6 client periodically sends out solicit packets on the local network, seeking an IPv6 router. 2.When an IPv6 router is present, it sends out an advertise packet in response to the solicit packet. This advertise packet informs the client that the IPv6 router is available for DHCP services. 3.The IPv6 client replies with a request packet to the DHCPv6 server, asking for an IPv6 configuration. 4.Finally, the DHCPv6 server issues the IPv6 configuration to the IPv6 client, which specifies several things, including the IP address, default gateway, DNS servers, etc. This is all included in the reply packet.Snatching Credentials with Mitm6
Using mitm6 is relatively simple, although it has quite a few options. For the most part to get it running, you can just simply run it using the following syntax:mitm6 -i interface
. Here's an expected output from running this: Because you've assigned systems an IPv6 address configuration, you will essentially need to either forward this traffic to another system or capture it and do something with it (i.e., impersonate a service to interact with the client).Important Note:
When using mitm6, it issues a DHCPv6 lease to clients that last for a period of 300 seconds (or 5 minutes). Due to this, it's possible that several DNS queries will actually fail, resulting in clients not being able to access services that rely on DNS names. You can, however, change this in the source code. Three common tools that can be combined with mitm6 are:Snarf
Snarf, written by Joshua Stone and Victor Mata, is an SMB relay tool that actually leaves an SMB relay session open for further use as opposed to simply running a command and destroying the relay session. When combined with mitm6, this tool can be extremely powerful. The ability to continue using relayed session without requiring re-authentication from the client gives you a lot of options.Responder
Responder is a tool developed by SpiderLabs to monitor the local network for NetBIOS Name Service (NBNS) and Link-Local Multicast Name Resolution (LLMNR) requests. Upon detecting this traffic, it sends spoofed replies to trick the system into communicating with the system running Responder. In addition to this, it also comes with a list of services that it can impersonate, such as Microsoft SQL (MSSQL), HTTP, LDAP, SMB, etc. So, any time someone tries to connect to these services on your system, they are essentially going to be interacting with Responder. Using mitm6 + Responder, you are essentially spoofing all (or specific) DNS requests, which will result in those systems landing in the hands of Responder. You can run Responder alongside mitm6 by using some of the default options as you usually would, such as Responder -I eth1ntlmrelayx
Ntlmrelayx can be used to relay credentials to systems that do not have SMB signing enforced. Ntlmrelayx also stands up an HTTP and SMB server. Any systems that attempt to access the SMB service running on your system (likely to happen as a result of mitm6), they are going to authenticate to ntlmrelayx, which will then relay this authentication attempt to a target of your choice. Ntlmrelayx can be run, in its minimal functionality, using the following syntax: /path/to/impacket/examples/ntlmrelayx.py -t smb://Recommendations
There are several recommendations that you can implement to help prevent or reduce the chances of these types of attacks. These recommendations can be applied to prevent rogue DHCP servers on both IPv4 and IPv6 networks.1.DHCP Snooping (IPv4)
- DHCP Snooping essentially drops IPv4 DHCP packets that are not originating from an authorized DHCP server. An authorized DHCP server is configured based on the switch's switchport as well as the MAC address of the legitimate DHCP server. In other words, just spoofing the MAC address alone does not equal to being able to offer DHCP requests. This could also be configured on a per VLAN basis.2.DHCPv6 Guard (IPv6)
- Similar to DHCP snooping, this essentially inspects packets between a DHCPv6 client and server, and drops them if they are not deemed legitimate.3.DHCPv6-Shield (IPv6)
- Also similar to DHCP snooping and is based on packet filtering at layer 2.4.Rogue Device Detection (IPv4 and IPv6)
- As usual, organizations should have visibility on their environment as it relates to newly connected devices. Not only would this help identify a potential rogue DHCP server, but also any other unknown devices on the network. There are many free and paid solutions out there to help organizations informed about the systems connected to their environment.5.Disable IPv6
- If IPv6 is not used within your organization, you can disable it altogether to prevent any devices from using it. As usual, all recommendations that suggest changes to your environment should be tested to reduce the likelihood of a negative impact within your environment. For any questions, reach out to us onFollow us:
Visit Medium :https://medium.com/@jamshed_hossain_mirazVisit Github :https://github.com/jamshedmiraz8
Visit Facebook page : https://www.facebook.com/jamshedhossainmiraz/
💬 Ask me about Cyber Security : jamshedmirazcontact@gmail.com
Visit in linkedin :https://www.linkedin.com/in/jamshed-hossain-miraz/
Portfolio Website :https://jamshedmiraz.000.pe/